Blogs
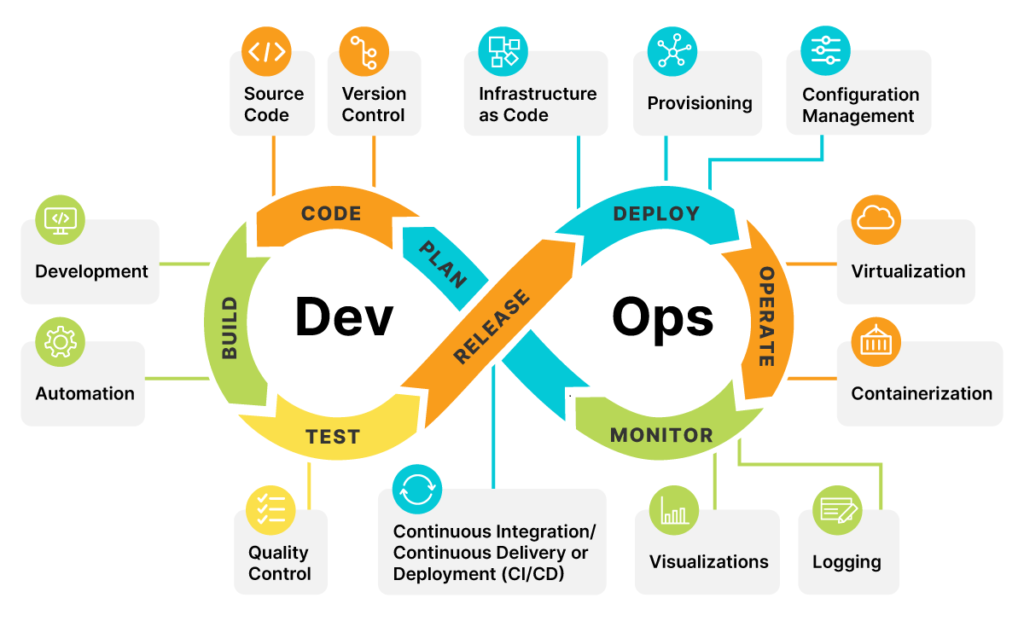
DevSecOps for Cloud Infrastructure: Integrating Security in CI/CD – A Pragmatic Guide for DevOps Teams
Introduction As organizations rapidly adopt cloud computing, microservices architecture, and containerized applications, DevOps teams are under increa…

7. Optimizing Cloud Costs Without Sacrificing Security – strategies to control cloud spend while maintaining compliance.
Introduction Cloud computing has become the backbone of modern digital infrastructure. Organizations across industries are rapidly adopting public clo…

Vendor Risk Management in Healthcare Cloud Environments: Securing Third-Party and Cloud Vendor Ecosystems
Introduction The healthcare industry is rapidly adopting cloud computing, digital health platforms, and third-party technology providers to improve pa…

Protecting Non-Traditional Healthcare Setups from Modern Digital Threats
Introduction Healthcare is no longer confined to hospital walls. Emergency response units, mobile clinics, pop-up medical camps, disaster-relief cente…

How AI-Driven Detection is Transforming Healthcare Security & Data Integrity
Introduction Electronic Medical Records (EMRs) have revolutionized healthcare by enabling faster access to patient data, improving care coordination,…

Telemedicine Security Essentials: Protecting Virtual Care Platforms from Modern Cyber Threats
A Complete Guide to Video Platform Security & Patient Data Protection Introduction Telemedicine has transformed healthcare delivery by enabling vi…
