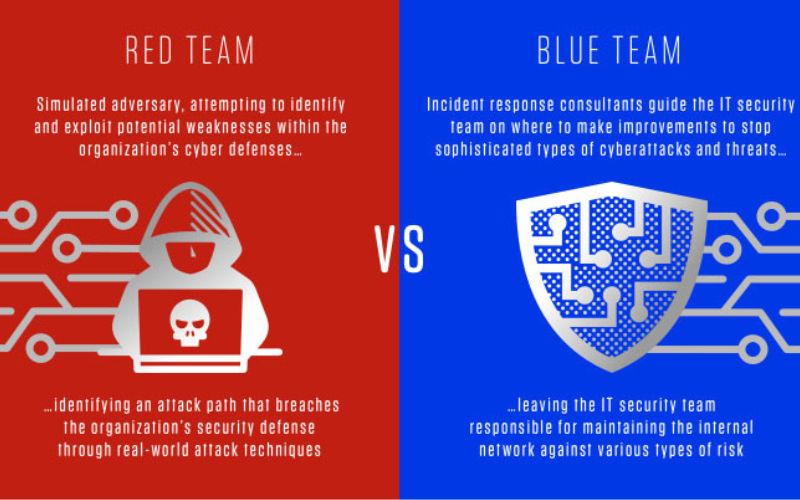
In today’s rapidly evolving threat landscape, organizations must stay ahead of cyberattacks—not react after damage is done. To strengthen a company’s security posture, cybersecurity teams across the world rely on two strategic approaches: Red Teaming and Blue Teaming.
While Red Teams focus on simulating real-world cyberattacks, Blue Teams specialize in detecting, defending, and responding to those attacks. Together, they create a powerful cybersecurity framework known as Purple Teaming, enabling organizations to proactively address risks and build a resilient defense.
In this blog, we break down the differences between Red Teaming and Blue Teaming, the role of penetration testing, defense strategies, and how businesses can leverage both approaches to harden their cybersecurity posture.
⭐ What Is Red Teaming?
Red Teaming is an offensive cybersecurity assessment where ethical hackers simulate advanced cyberattacks to uncover vulnerabilities before real attackers exploit them.
✔ Key Objectives of a Red Team:
-
Identify exploitable weaknesses in systems, networks, and applications
-
Simulate tactics used by real-world threat actors
-
Test the effectiveness of existing security controls
-
Assess how quickly the organization detects and responds to attacks
-
Provide actionable remediation insights
???? Common Red Team Techniques:
-
Social engineering
-
Network penetration attacks
-
Exploiting misconfigurations
-
Phishing and spear-phishing
-
Privilege escalation
-
Lateral movement
-
Web application attacks
-
Breach and attack simulation
Red Teaming goes beyond traditional penetration testing by focusing on realistic attack scenarios and measuring the organization’s actual resilience.
⭐ What Is Blue Teaming?
Blue Teaming is a defensive cybersecurity strategy where security professionals continuously monitor, detect, respond to, and neutralize cyber threats.
✔ Key Objectives of a Blue Team:
-
Strengthen internal security controls
-
Monitor network and endpoint activity
-
Detect suspicious behavior and anomalies
-
Mitigate attacks in real-time
-
Conduct incident response and forensics
-
Ensure compliance and risk management
???? Common Blue Team Tools & Techniques:
-
SIEM monitoring (Security Information & Event Management)
-
EDR/XDR platforms
-
Threat hunting
-
Log analysis
-
Vulnerability management
-
Firewall tuning
-
Identity & access management (IAM)
-
Patch management
-
Security operations (SOC)
-
Incident response playbooks
Blue Teams focus on continuous defense, building layers of protection that prevent and contain threats.

⭐ Red Team vs Blue Team: Key Differences
| Feature | Red Team | Blue Team |
|---|---|---|
| Approach | Offensive (Attack simulation) | Defensive (Detection & response) |
| Goal | Identify vulnerabilities | Protect and secure the environment |
| Method | Ethical hacking, exploitation | Monitoring, threat hunting, remediation |
| Outcome | Security gaps report | Incident mitigation & security hardening |
| Focus | Breaking in | Keeping attackers out |
Both teams serve opposite purposes but share one mission—enhancing the organization's cybersecurity posture.
⭐ How Red Teaming Helps Strengthen Security
Red Teaming reveals how well your system holds up against real cyber threats.
???? Benefits:
-
Identifies real-world vulnerabilities
-
Improves risk awareness
-
Validates security controls
-
Enhances incident response readiness
-
Shows blind spots in networks, endpoints, and employee behavior
Organizations that conduct red team assessments regularly stay one step ahead of attackers.
⭐ How Blue Teaming Protects Your Infrastructure
Blue Teams create a robust security framework that prevents cyberattacks from succeeding.
???? Benefits:
-
Real-time threat detection
-
Stronger incident response
-
Reduced attack surface
-
Continuous monitoring and compliance
-
Improved data protection
Blue Teaming makes your cybersecurity approach proactive, not reactive.
⭐ Where Pen-Testing Fits In: Red Teaming vs Penetration Testing
Many people confuse penetration testing with Red Teaming, but they serve different purposes.
✔ Penetration Testing (Pen-Testing):
-
Targets a specific system or application
-
Aims to find vulnerabilities
-
Usually short-term
-
Follows a structured testing methodology
✔ Red Teaming:
-
Simulates real-world attacks
-
Tests people, processes, and technology
-
Long-term engagements
-
Measures detection and response capabilities
Pen-testing = finding vulnerabilities
Red Teaming = understanding overall security resilience
⭐ Purple Teaming: The Best of Both Worlds
Purple Teaming integrates Red Team offensive tactics with Blue Team defensive strategies to create a collaborative approach.
✔ Benefits of Purple Teaming:
-
Faster vulnerability remediation
-
Improved security control effectiveness
-
Shared knowledge among security teams
-
Stronger organizational security posture
This approach ensures continuous learning and better alignment between attack simulation and defense.
⭐ Why Growing Businesses Must Implement Red & Blue Team Strategies
As cyber threats increase in sophistication, businesses cannot rely on outdated defenses.
Red Teaming and Blue Teaming help companies:
-
Identify and patch vulnerabilities
-
Improve SOC efficiency
-
Strengthen cloud and network security
-
Prevent data breaches
-
Reduce financial and operational risks
-
Maintain compliance (ISO 27001, GDPR, PCI-DSS, etc.)
Whether you are an SME or a large enterprise, both teams play a crucial role in building cyber resilience.
⭐ Why Choose Gigahertz Consultants for Red Teaming & Blue Teaming Services?
Gigahertz Consultants offers end-to-end cybersecurity services designed to protect modern businesses against evolving threats.
✔ Our Capabilities Include:
-
Comprehensive Red Team assessments
-
24/7 SOC monitoring (Blue Team operations)
-
Penetration testing (internal, external, cloud, web, mobile)
-
Threat hunting & incident response
-
Vulnerability assessments
-
Cloud security audits
-
Cyber maturity & risk assessment
-
Zero-trust security design
-
Compliance and governance support
We simulate real-world attacks, strengthen your defenses, and ensure your business stays resilient against all forms of cyber threats.
Conclusion
Cybersecurity is no longer a luxury—it is a necessity for every growing business.
By combining the offensive strength of Red Teams and the defensive expertise of Blue Teams, organizations can create a strong, future-ready security posture that withstands modern cyber threats.
Whether you want to test your defenses, strengthen your SOC, or build a long-term cybersecurity roadmap, Gigahertz Consultants provides the expertise and advanced tools your business needs to stay protected.

Category: Cybersecurity
