In today’s fast-evolving digital landscape, cybersecurity is no longer a luxury but a necessity for every business. For small and medium enterprises (SMEs), the stakes are even higher—limited resources, growing reliance on cloud services, and the increasing sophistication of cyber threats make it critical to adopt a modern security model. One of the most effective approaches gaining momentum worldwide is the Zero Trust Security Framework.
But what exactly is Zero Trust, and how can SMEs practically implement it without overburdening their budgets or teams? This blog provides a step-by-step roadmap tailored for small and medium businesses to begin their Zero Trust journey.
What is Zero Trust Security?
Zero Trust is a cybersecurity model that assumes no user, device, or application—whether inside or outside the corporate network—can be automatically trusted. Instead, every access request is continuously verified based on identity, context, and compliance with organizational policies.
Key principles of Zero Trust include:
-
Verify explicitly: Always authenticate and authorize users and devices.
-
Least privilege access: Grant only the permissions necessary for specific tasks.
-
Assume breach: Design defenses assuming attackers may already be inside your network.
For SMEs, adopting Zero Trust provides a strong cyber resilience strategy against data breaches, ransomware attacks, insider threats, and third-party risks.
Why Zero Trust Matters for SMEs
Many SMEs believe Zero Trust Security is too complex or designed only for large enterprises. However, this is a misconception. In fact:
-
Cybercriminals increasingly target SMEs because of weaker defenses.
-
A single cyber attack can lead to significant financial losses and reputational damage.
-
SMEs are adopting cloud services, SaaS applications, and remote work models, which require robust security controls.
-
Regulatory compliance (GDPR, HIPAA, ISO 27001, etc.) is easier to achieve with Zero Trust practices.
By implementing Zero Trust, SMEs can protect sensitive data, ensure business continuity, and build customer trust.
Practical Roadmap: How SMEs Can Start with Zero Trust
Implementing Zero Trust does not mean replacing your entire IT infrastructure overnight. Instead, SMEs should take a phased approach. Here’s a practical Zero Trust roadmap:
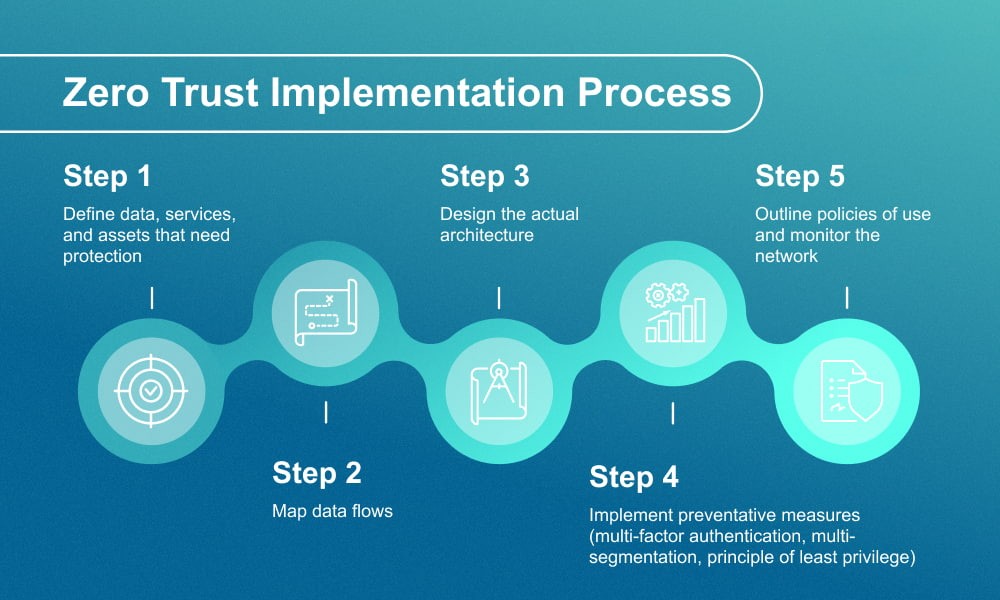
1. Assess Your Current Security Posture
-
Conduct a risk assessment of your IT environment.
-
Identify critical assets such as customer data, financial records, intellectual property, and cloud workloads.
-
Map out existing users, devices, applications, and data flows.
2. Secure User Identities with Strong Authentication
-
Implement Multi-Factor Authentication (MFA) for all employees, contractors, and partners.
-
Adopt Single Sign-On (SSO) to reduce password fatigue.
-
Regularly review and update identity and access management (IAM) policies.
3. Enforce Least Privilege Access
-
Apply Role-Based Access Control (RBAC) to ensure employees access only what they need.
-
Continuously monitor user activities for anomalous behavior.
-
Revoke unused or outdated accounts immediately.
4. Protect Endpoints and Devices
-
Use endpoint detection and response (EDR) tools.
-
Keep all devices updated with patch management.
-
Enforce mobile device management (MDM) policies for remote workers.
5. Segment Networks and Applications
-
Implement micro-segmentation to reduce lateral movement of attackers.
-
Isolate critical workloads such as finance systems, HR data, and customer portals.
-
Use firewalls and secure gateways to control traffic between segments.
6. Monitor, Detect, and Respond Continuously
-
Deploy a Security Information and Event Management (SIEM) system for real-time visibility.
-
Use threat intelligence to stay ahead of cyber risks.
-
Regularly conduct penetration testing and vulnerability assessments.
7. Build a Security-First Culture
-
Conduct employee training on phishing, social engineering, and password hygiene.
-
Establish incident response plans for quick recovery.
-
Promote accountability and awareness across the organization.
Common Challenges SMEs Face in Zero Trust Implementation
-
Limited budgets: Start small—focus on identities and endpoints first.
-
Lack of expertise: Consider partnering with a Managed Security Services Provider (MSSP).
-
Resistance to change: Educate teams on the long-term benefits of cyber resilience.
Zero Trust and Compliance
Zero Trust also helps SMEs align with major cybersecurity regulations and frameworks, including:
-
GDPR (General Data Protection Regulation)
-
ISO 27001 Information Security Management System
-
NIST Cybersecurity Framework
-
HIPAA (for healthcare organizations)
By following Zero Trust practices, SMEs not only reduce risks but also simplify audits and compliance reporting.
Key Benefits of Zero Trust for SMEs
-
Enhanced protection against cyber attacks
-
Secure remote work for employees and contractors
-
Simplified compliance and audit readiness
-
Better visibility into users, devices, and applications
-
Reduced business risk and downtime
Conclusion
For SMEs, Zero Trust Security is no longer optional—it’s essential for staying competitive in a world where cyber threats are constant and evolving. By following this step-by-step Zero Trust implementation roadmap, small and medium businesses can gradually build a robust cybersecurity foundation without overwhelming their resources.
Remember: Zero Trust is a journey, not a one-time project. Start small, scale wisely, and continuously improve.
At Gigahertz Consultants, we help SMEs implement Zero Trust frameworks, endpoint security, identity management, and compliance solutions tailored to their business needs.

Category: General - CyberSecurity
