Blogs

Protecting Non-Traditional Healthcare Setups from Modern Digital Threats
Introduction Healthcare is no longer confined to hospital walls. Emergency response units, mobile clinics, pop-up medical camps, disaster-relief cente…

How AI-Driven Detection is Transforming Healthcare Security & Data Integrity
Introduction Electronic Medical Records (EMRs) have revolutionized healthcare by enabling faster access to patient data, improving care coordination,…

Telemedicine Security Essentials: Protecting Virtual Care Platforms from Modern Cyber Threats
A Complete Guide to Video Platform Security & Patient Data Protection Introduction Telemedicine has transformed healthcare delivery by enabling vi…

Insider Threat Detection: Beyond Logs and Alerts – Proactive Detection Strategies with a Human-Factor Focus
Cybersecurity discussions often revolve around external attackers—hackers, ransomware groups, and cybercriminals. But some of the most dangerous threa…

Cybersecurity Maturity Model Integration (CMMI) for SMEs – Building Long-Term Resilience
In an era where cyberattacks are increasing in frequency, sophistication, and financial impact, Small and Medium Enterprises (SMEs) face greater risks…
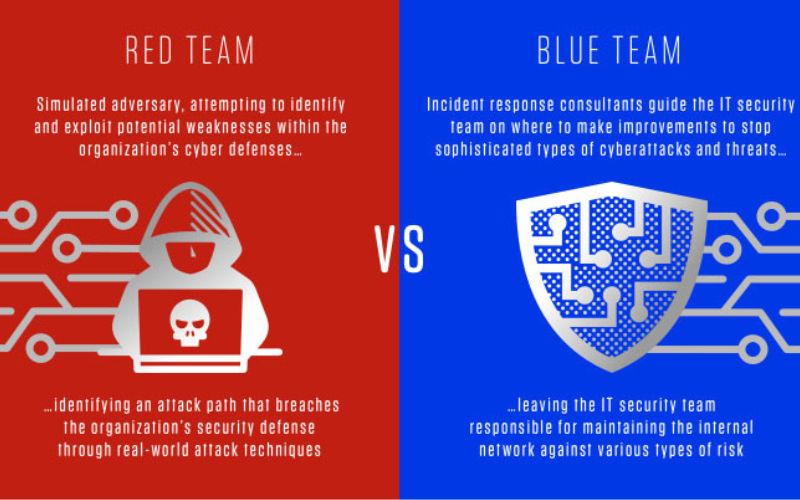
Red Teaming vs Blue Teaming: How to Harden Your Security Posture – Pen-Testing vs Defense Strategies Explained
In today’s rapidly evolving threat landscape, organizations must stay ahead of cyberattacks—not react after damage is done. To strengthen a company’s …
